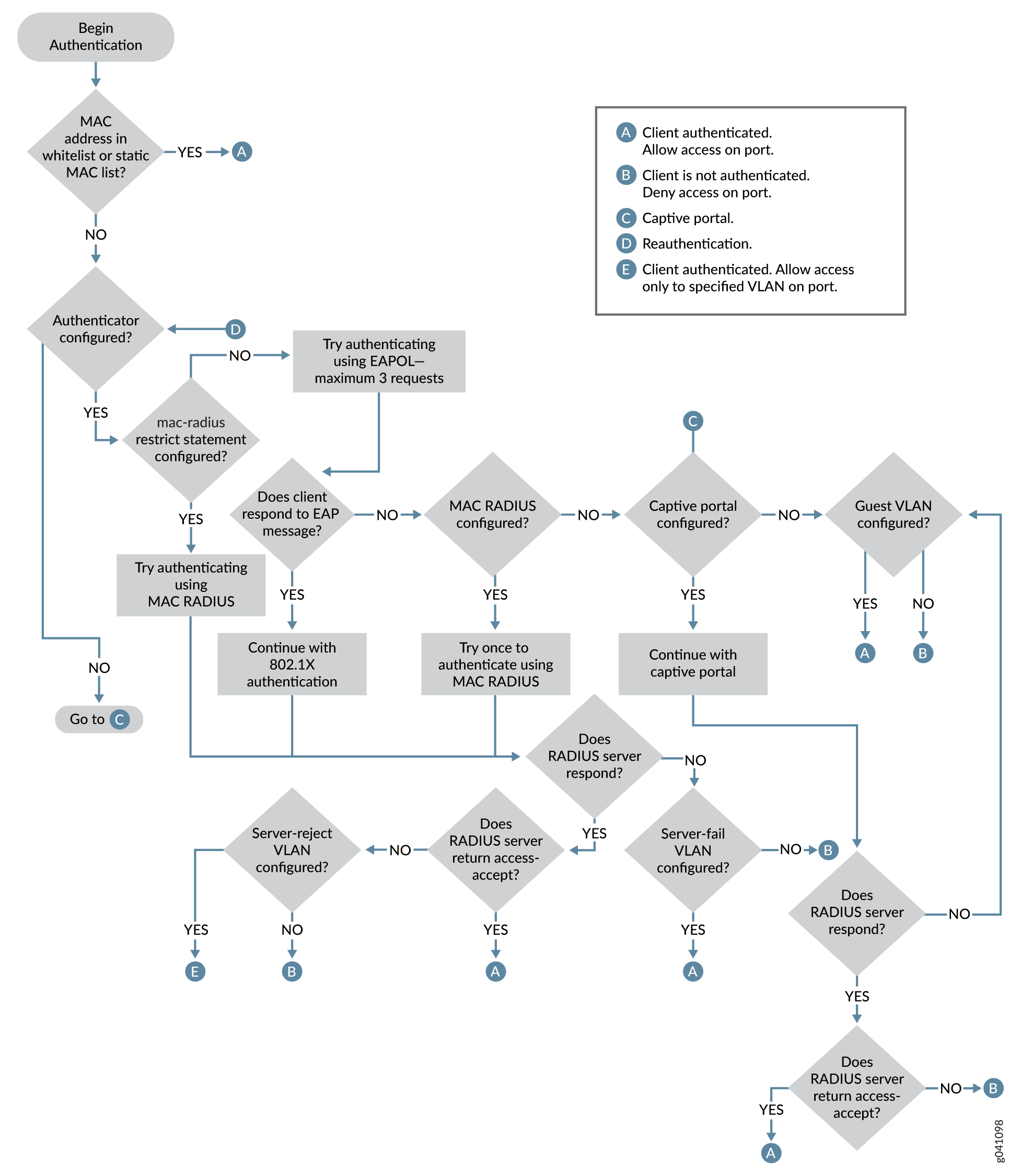
Authentication Process Flow for MX Series Routers in Enhanced LAN Mode | User Access and Authentication Administration Guide | Juniper Networks TechLibrary

Example for Configuring RADIUS Authentication and Accounting - AR100, AR120, AR150, AR160, AR200, AR1200, AR2200, AR3200, and AR3600 V200R010 CLI-based Configuration Guide - Security - Huawei

Linksys Official Support - What are Authentication Types, Basic Rate and Transmission Rate and how to Enable or Disable them

5Port Gigabit AC Authentication Gateway Routing, Multi WAN Load balance Core Gateway wifi project router VPN Router Wired Router|Wired Routers| - AliExpress

(3).jpg)

![Draytek ] Use 802.1X authentication for wireless clients with Local 802.1X | NETVN - YouTube Draytek ] Use 802.1X authentication for wireless clients with Local 802.1X | NETVN - YouTube](https://i.ytimg.com/vi/g05EXSvxRqo/maxresdefault.jpg)